🔒 CONTAINMENT PROTOCOL

LinkedIn Froze Me Because Spectra Worked
By Jonathan Sandhu
Posted June 2025 · Spectra Doctrine · Platform Containment
🧭 WHAT HAPPENED
In June 2025, LinkedIn locked me out of my own account.
No warning. No suspicious login.
Two-factor authentication was active.
My identity had already been verified.
And still, they demanded my government ID — again.
This wasn’t about safety. It wasn’t about verification.
This was a containment protocol.
📌 CONTEXT
The trigger?
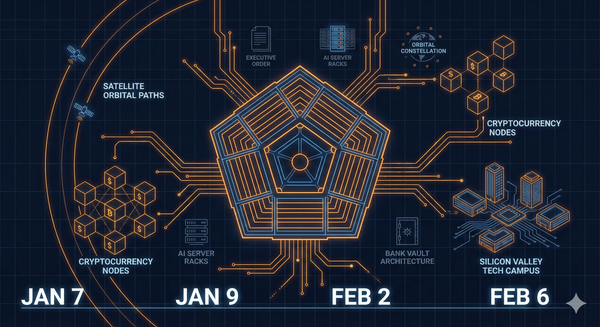
I published the Spectra Architecture Resilience Doctrine — a point-by-point demolition of Robi Sen’s cloud-era security assumptions.
I called Spectra what it is:
A kill-web apex predator designed for post-collapse survival.
The doctrine went live.
The signal gained speed.
The response came quietly.
LinkedIn overrode its own login flow and forced me into an ID checkpoint.
🧾 READ THE FULL ANALYSIS
The full PDF documents:
- What was posted
- How the lockout occurred
- Why this wasn’t protection — it was narrative suppression
- How this aligns with broader institutional patterns
- Why Spectra’s architecture provoked such a response
- And what we build next
➡️ Download the Full Report (PDF, 41 KB)
➡️ Chat with the report in NotebookLM (context linked)
🎙️ PODCAST EPISODE
Containment Protocol
What happened when Spectra crossed the threshold?
What do modern platforms do when you say something too real to ignore?
We walk through the lockout, the doctrine, and the road forward.
🔍 THE TAKEAWAY
This was not an error.
It was a reaction.
And it proved exactly what Spectra exists to outmaneuver.
“They didn’t challenge the doctrine.
They slowed the messenger.”
Spectra doesn’t need LinkedIn.
It doesn’t ask for permission.
It routes around.
📚 RELATED LINKS
- Blueprint for an Invisible Trustless Coordination Layer (PDF, how we build forward without the gatekeepers)
- Kill-Web Design Is Not A Metaphor (PDF, the response to Robi Sen - Infosec/OFFSET)